Week 22, 2021 - Tips I learned this week
IntelliSense in vscode, Azure CLI command to get assigned roles, and Azure Storage Explorer new version.
This week I learned some Azure CLI commands, how to have json IntelliSense in vscode and that Azure Storage Explorer was usable again.
Autocompletion and schema validation when editing a json file in vscode.
When you are editing a json file in vscode, chances are that there is a json schema somewhere that describes the shape of the json you are modifying. Wouldn't it be great if vscode could provide you suggestions and validate the json according to such a schema while you are typing ⌨?
Well in fact it is possible, you just have to add at the beginning of your file a $schema key (with the URI of the json schema as the value) and you will have IntelliSense to edit your json in vscode.
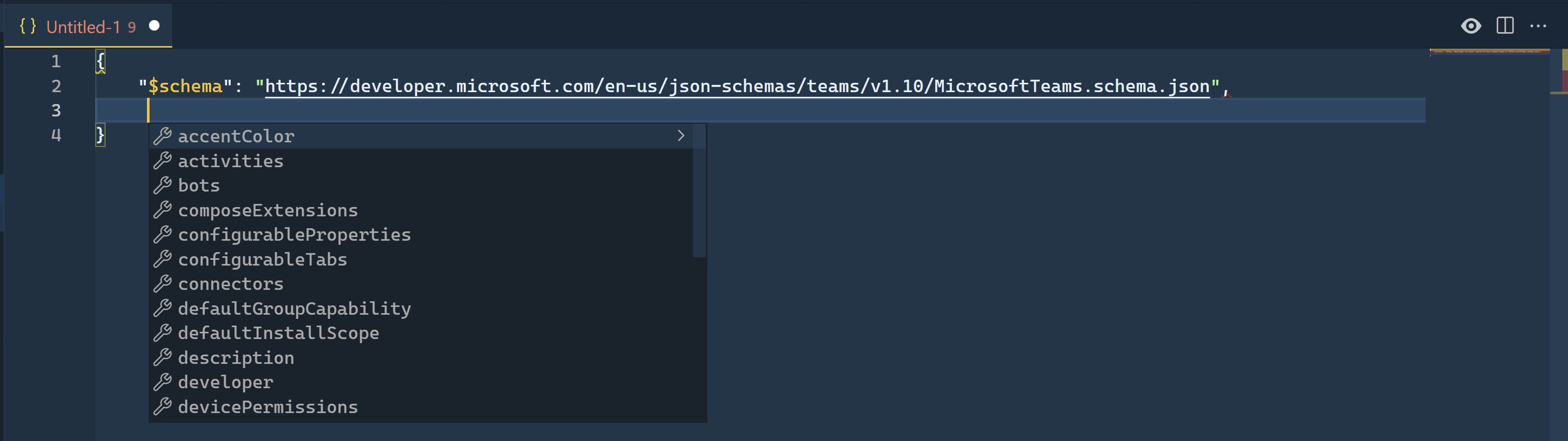
In the screenshot above, I am editing a json file where the linked json schema is a Microsoft Teams app manifest schema and as you can see vscode gives me suggestions based on this schema.
This is a tip that you probably already know but as far as I am concerned I only discovered it recently and it is really useful. If you want do to more advanced things like mapping some files types to specific json schemas you can have a look in vscode documentation.
Listing assigned roles for a user on a subscription with Azure CLI
I recently had to list all the roles assigned to my user on a subscription. 👮♀️ For that I used the az role assignement list command like this:
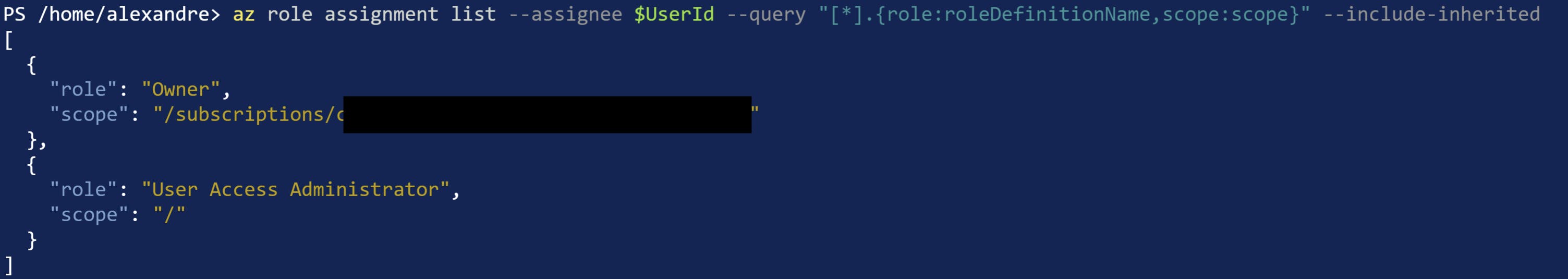
I am filtering the command result with the --query argument to only have the information I am interested in which are roleDefinitionName and scope.
You can specify a subscription by using the optional parameter --subscription but by default the subscription selected is the current subscription which you can see by doing an az account show.
The variable UserId which is passed to the option --assignee contains my user id but I could have also passed my user principal name. As I was looking to list my assigned roles on a subscription in a tenant id where I am a guest, my user principal name is a bit strange with an #EXT# in it so I can never remember what it is. And as I don't know by heart my user id either, I use the az ad signed-in-user show command to get my user id.
So at the end my command to list the assigned roles to my user on the current subscription is the following:
az role assignment list --assignee $(az ad signed-in-user show --query "objectId") --query "[*].{role:roleDefinitionName,scope:scope}" --include-inherited
Azure Storage Explorer just got better !
Azure Storage Explorer is a tool to manage you Azure cloud storage resources from your desktop. Instead of going to Azure portal and navigating between all the panes and resources, you can do everything from this tool like viewing the tables and blobs in the storage accounts you have access to.
Unfortunately, if your account had access to multiple subscriptions on multiple tenants with MFA enabled, using Azure Storage Explorer was a nightmare where you had to log in to a every tenant multiple times to access any storage account. I you had the correct permissions you ended up grabbing a secret connection string to access your storage account from Azure Storage Explorer but it was not a good solution (using secrets instead of your Azure AD account to access resources is never a good idea ⛔).
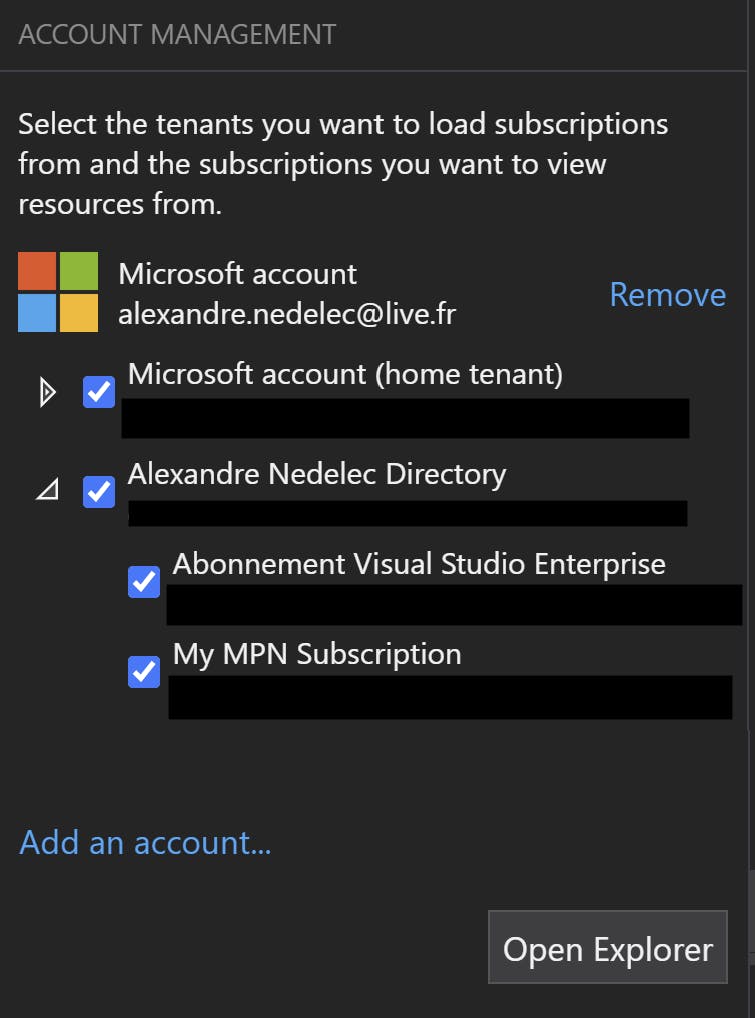
As you can see on the screenshot above, in v1.19.x Azure Storage Explorer account management section has been completely refreshed to allow us to control exactly the tenants and the subscriptions that we want to load. This way we only have to enter the credentials we need and Azure Storage Explorer becomes usable again! 🎉
And that's it for this week, happy learning!
